What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-02-02 21:29:09 | NEWS WRAP-UP: Dutch spies corroborate Russia\'s meddling in U.S. election - and 19 EU nations (lien direct) | Week ending Feb. 2, 2018. Even more substantive corroborating evidence of Russia's proactive interference in the 2016 U.S. presidential election comes from the Netherlands. European news reports detail how a Dutch intelligence agency secretly hacked into the Kremlin's most notorious hacking group, Cozy Bear, and tracked Cozy Bear's election tampering activities. Dutch spies passed all […] | APT 29 | |||
| 2018-01-28 13:23:51 | Les services secrets néerlandais infiltrent Cozy Bear (lien direct) | >Fume, c’est du Cozy Bear ! Les services de renseignement néerlandais auraient fourni des preuves cruciales à leurs homologues américains sur l’ingérence de la Russie lors des élections de 2016. Voilà qui est intéressant. Les services secrets américains ne seraient pas les auteurs des inf... Cet article Les services secrets néerlandais infiltrent Cozy Bear est apparu en premier sur ZATAZ. | APT 29 | |||
| 2018-01-26 17:05:41 | The Dutch were spying on Cozy Bear Hackers as they targeted Democrats (lien direct) | Dutch intelligence is claiming to have observed Russian state-sponsored hackers known as Cozy Bear attacking Democratic Party organizations in the U.S. beginning in 2014. A shocking report from a Dutch website, de Volkskrant, claims that hackers from that country’s intelligence community penetrated the network of a building used by...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/520448790/0/thesecurityledger -->» | APT 29 | |||
| 2018-01-26 14:45:00 | Dutch Intel Agency Reportedly Helped US Attribute DNC Hack to Russia (lien direct) | The General Intelligence and Security Service of the Netherlands broke into Cozy Bear's network in 2014 and spotted the group launching attacks, de Volkskrant says. | APT 29 | |||
| 2018-01-26 11:37:18 | Dutch intelligence agency spied on and took photos of Russia-linked Cozy Bear hackers (lien direct) | >In 2014, Dutch intelligence agency AIVD reportedly managed to locate the hub of the Kremlin-linked hacker group Cozy Bear, also known as APT29. AIVD reportedly gained access to the state-sponsored hacker group’s networks and spied on Cozy Bear’s hacking activities in a cyberespionage campaign that is believed to have lasted between one and two and ... | APT 29 | ★★ | ||
| 2018-01-26 10:40:29 | The Dutch intelligence service AIVD \'hacked\' Russian Cozy Bear systems for years (lien direct) | Spying on spies – The hackers from the Dutch intelligence service AIVD ‘compromised’ for years the network of the Russian APT Cozy Bear. It’s not a mystery, technology firms that intend to work with Russia need to allow the Government experts to scan their code for backdoors and vulnerabilities. The problem is that this software […] | APT 29 | |||
| 2017-04-05 22:57:33 | Part II. APT29 Russian APT including Fancy Bear (lien direct) |  This is the second part of Russian APT series."APT29 - The Dukes Cozy Bear: APT29 is threat group that has been attributed to the Russian government and has operated since at least 2008.1210 This group reportedly compromised the Democratic National Committee starting in the summer of 2015" (src. Mitre ATT&CK)Please see the first post here: Russian APT - APT28 collection of samples including OSX XAgentI highly recommend reading and studying these resources first:Mitre ATT&CK2017-03 Disinformation. A Primer In Russian Active Measures And Influence Campaigns. Hearings before the Select Committee on Intelligence, March 20172014-08 Mikko Hipponen. Governments as Malware Authors. Presentation ppt.2016. No Easy Breach: Challenges and Lessons from an Epic Investigation. Mandiant. Matthew Dunwoody, Nick Carr. VideoBeyond 'Cyber War': Russia's Use of Strategic Cyber Espionage and Information Operations in Ukraine. NATO Cooperative Cyber Defence Centre of Excellence/ Fireeye - Jen WeedonList of References (and samples mentioned) listed from oldest to newest:2012-02 FSecure. COZYDUKE2013-02_Crysys_Miniduke Indicators2013-04_Bitdefender_A Closer Look at MiniDuke2014-04 FSecure_Targeted Attacks and Ukraine2014-05_FSecure.Miniduke still duking it out2014-07_Kaspersky_Miniduke is back_Nemesis Gemina and the Botgen Studio2014-07_Kaspersky_The MiniDuke Mystery PDF 0-day2014-11_FSecure_OnionDuke APT Attacks Via the Tor Network2014_FSecure_Cosmicduke Cosmu with a twist of MiniDuke2015-04_Kaspersky_CozyDuke-CozyBear This is the second part of Russian APT series."APT29 - The Dukes Cozy Bear: APT29 is threat group that has been attributed to the Russian government and has operated since at least 2008.1210 This group reportedly compromised the Democratic National Committee starting in the summer of 2015" (src. Mitre ATT&CK)Please see the first post here: Russian APT - APT28 collection of samples including OSX XAgentI highly recommend reading and studying these resources first:Mitre ATT&CK2017-03 Disinformation. A Primer In Russian Active Measures And Influence Campaigns. Hearings before the Select Committee on Intelligence, March 20172014-08 Mikko Hipponen. Governments as Malware Authors. Presentation ppt.2016. No Easy Breach: Challenges and Lessons from an Epic Investigation. Mandiant. Matthew Dunwoody, Nick Carr. VideoBeyond 'Cyber War': Russia's Use of Strategic Cyber Espionage and Information Operations in Ukraine. NATO Cooperative Cyber Defence Centre of Excellence/ Fireeye - Jen WeedonList of References (and samples mentioned) listed from oldest to newest:2012-02 FSecure. COZYDUKE2013-02_Crysys_Miniduke Indicators2013-04_Bitdefender_A Closer Look at MiniDuke2014-04 FSecure_Targeted Attacks and Ukraine2014-05_FSecure.Miniduke still duking it out2014-07_Kaspersky_Miniduke is back_Nemesis Gemina and the Botgen Studio2014-07_Kaspersky_The MiniDuke Mystery PDF 0-day2014-11_FSecure_OnionDuke APT Attacks Via the Tor Network2014_FSecure_Cosmicduke Cosmu with a twist of MiniDuke2015-04_Kaspersky_CozyDuke-CozyBear |
APT 29 APT 28 | |||
| 2017-04-03 12:42:42 | APT29 Uses Stealthy Backdoor to Maintain Access to Targets (lien direct) | Researchers at FireEye-owned Mandiant have conducted a detailed analysis of a stealthy backdoor used by the Russia-linked cyberespionage group APT29 to maintain access to targeted systems. | APT 29 | |||
| 2017-04-03 07:00:00 | Dissection de l'une des boursiers WMI et PowerShell sans fichu et PowerShell (Poshspy) Dissecting One of APT29\\'s Fileless WMI and PowerShell Backdoors (POSHSPY) (lien direct) |
Mandiant a observé APT29 en utilisant une porte dérobée furtive que nous appelons poshspy.Poshspy exploite deux des outils que le groupe utilise fréquemment: PowerShell et Windows Management Instrumentation (WMI).Dans les enquêtes que Mandiant a menées, il est apparu qu'APT29 a déployé Poshspy comme porte dérobée secondaire pour une utilisation s'ils perdaient l'accès à leurs possibilités principales.
Poshspy tire le meilleur parti des fonctionnalités Windows intégrées & # 8211;Ce que l'on appelle «vivre du terrain» & # 8211;pour faire une porte dérobée particulièrement furtive.L'utilisation de WMI de Poshspy \\ pour stocker et persister le code de porte dérobée le rend presque invisible pour quiconque
Mandiant has observed APT29 using a stealthy backdoor that we call POSHSPY. POSHSPY leverages two of the tools the group frequently uses: PowerShell and Windows Management Instrumentation (WMI). In the investigations Mandiant has conducted, it appeared that APT29 deployed POSHSPY as a secondary backdoor for use if they lost access to their primary backdoors. POSHSPY makes the most of using built-in Windows features – so-called “living off the land” – to make an especially stealthy backdoor. POSHSPY\'s use of WMI to both store and persist the backdoor code makes it nearly invisible to anyone |
Tool Technical | APT 29 | ★★★★ | |
| 2017-03-31 02:03:28 | Part I. Russian APT - APT28 collection of samples including OSX XAgent (lien direct) |  This post is for all of you, Russian malware lovers/haters. Analyze it all to your heart's content. Prove or disprove Russian hacking in general or DNC hacking in particular, or find that "400 lb hacker" or nail another country altogether. You can also have fun and exercise your malware analysis skills without any political agenda.The post contains malware samples analyzed in the APT28 reports linked below. I will post APT29 and others later.Read about groups and types of targeted threats here: Mitre ATT&CKList of References (and samples mentioned) listed from oldest to newest:APT28_2011-09_Telus_Trojan.Win32.Sofacy.AAPT28_2014-08_MhtMS12-27_PrevenityAPT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.OperationsAPT28_2014-10_Telus_Coreshell.AAPT28_2014-10_TrendMicro Operation Pawn Storm. Using Decoys to Evade DetectionAPT28_2015-07_Digital Attack on German ParliamentAPT28_2015-07_ESET_Sednit_meet_HackingAPT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.BAPT28_2015-09_Root9_APT28_Technical_FollowupAPT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-codeAPT28_2015-10_New Adobe Flash Zero-Day Used in Pawn StormAPT28_2015-10_Root9_APT28_targets Financial MarketsAPT28_2015-12_Bitdefender_In-depth_anal This post is for all of you, Russian malware lovers/haters. Analyze it all to your heart's content. Prove or disprove Russian hacking in general or DNC hacking in particular, or find that "400 lb hacker" or nail another country altogether. You can also have fun and exercise your malware analysis skills without any political agenda.The post contains malware samples analyzed in the APT28 reports linked below. I will post APT29 and others later.Read about groups and types of targeted threats here: Mitre ATT&CKList of References (and samples mentioned) listed from oldest to newest:APT28_2011-09_Telus_Trojan.Win32.Sofacy.AAPT28_2014-08_MhtMS12-27_PrevenityAPT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.OperationsAPT28_2014-10_Telus_Coreshell.AAPT28_2014-10_TrendMicro Operation Pawn Storm. Using Decoys to Evade DetectionAPT28_2015-07_Digital Attack on German ParliamentAPT28_2015-07_ESET_Sednit_meet_HackingAPT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.BAPT28_2015-09_Root9_APT28_Technical_FollowupAPT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-codeAPT28_2015-10_New Adobe Flash Zero-Day Used in Pawn StormAPT28_2015-10_Root9_APT28_targets Financial MarketsAPT28_2015-12_Bitdefender_In-depth_anal |
APT 29 APT 28 | |||
| 2017-03-27 20:14:12 | APT29 Used Domain Fronting, Tor to Execute Backdoor (lien direct) | APT29, a/k/a Cozy Bear, has used Tor and a technique called domain fronting in order to secure backdoor access to targets for nearly two years running. | APT 29 | |||
| 2017-03-27 14:56:43 | APT29 Cyberspies Use Domain Fronting to Evade Detection (lien direct) | The Russia-linked cyber espionage group known as APT29 has been using a technique called “domain fronting†in an effort to make it more difficult for targeted organizations to identify malicious traffic, FireEye reported on Monday. | APT 29 | |||
| 2017-03-27 07:00:00 | Domaine APT29 Fonctionner avec Tor APT29 Domain Fronting With TOR (lien direct) |
Mandiant a observé que les attaquants de l'État-nation russe APT29 employant des techniques de façade de domaine pour l'accès de porte dérobée furtif aux environnements victimes pendant au moins deux ans.Il y a eu des discussions considérables sur le fronoisement du domaine après la publication d'un document détaillant ces techniques .Domain Fronting fournit des connexions de réseau sortant qui ne se distinguent pas des demandes légitimes de sites Web populaires.
APT29 a utilisé le routeur d'oignon (TOR) et le plugin de façade du domaine Tor Mode pour créer un tunnel réseau crypté caché qui semblait se connecter aux services Google sur TLS
Mandiant has observed Russian nation-state attackers APT29 employing domain fronting techniques for stealthy backdoor access to victim environments for at least two years. There has been considerable discussion about domain fronting following the release of a paper detailing these techniques. Domain fronting provides outbound network connections that are indistinguishable from legitimate requests for popular websites. APT29 has used The Onion Router (TOR) and the TOR domain fronting plugin meek to create a hidden, encrypted network tunnel that appeared to connect to Google services over TLS |
APT 29 APT 29 | ★★★★ | ||
| 2017-02-13 16:52:34 | DHS Uses Cyber Kill Chain to Analyze Russia-Linked Election Hacks (lien direct) | DHS Publishes Enhanced Analysis Report on GRIZZLY STEPPE Activity | APT 29 APT 28 | |||
| 2017-01-11 04:00:46 | 10 Questions that Need to Be Asked about Every Cybersecurity Story (lien direct) | The Russian hacking fiasco we’ve been following over the past weeks – hysteria, which is due to the flawed Grizzly Steppe report and subsequent haphazard news reporting – has done a grave disservice to the serious issue of national cybersecurity. If the world is going to ever turn the corner from its current state of […]… Read More | APT 29 APT 28 | |||
| 2017-01-04 17:40:00 | DHS-FBI Report Shows Russian Attribution\'s A Bear (lien direct) | Political and technical fallout from the DHS-FBI joint 'Grizzly Steppe' report on Russia's role in the recent election-related hacks causes more chaos than closure. | APT 29 APT 28 | |||
| 2017-01-03 21:33:01 | Dear Obama, From Infosec (lien direct) | Dear President Obama:We are more than willing to believe Russia was responsible for the hacked emails/records that influenced our election. We believe Russian hackers were involved. Even if these hackers weren't under the direct command of Putin, we know he could put a stop to such hacking if he chose. It's like harassment of journalists and diplomats. Putin encourages a culture of thuggery that attacks opposition, without his personal direction, but with his tacit approval.Your lame attempts to convince us of what we already agree with has irretrievably damaged your message.Instead of communicating with the America people, you worked through your typical system of propaganda, such as stories in the New York Times quoting unnamed "senior government officials". We don't want "unnamed" officials -- we want named officials (namely you) who we can pin down and question. When you work through this system of official leaks, we believe you have something to hide, that the evidence won't stand on its own.We still don't believe the CIA's conclusions because we don't know, precisely, what those conclusions are. Are they derived purely from companies like FireEye and CloudStrike based on digital forensics? Or do you have spies in Russian hacker communities that give better information? This is such an important issue that it's worth degrading sources of information in order to tell us, the American public, the truth.You had the DHS and US-CERT issue the "GRIZZLY-STEPPE" report "attributing those compromises to Russian malicious cyber activity". It does nothing of the sort. It's full of garbage. It contains signatures of viruses that are publicly available, used by hackers around the world, not just Russia. It contains a long list of IP addresses from perfectly normal services, like Tor, Google, Dropbox, Yahoo, and so forth.Yes, hackers use Yahoo for phishing and malvertising. It doesn't mean every access of Yahoo is an "Indicator of Compromise".For example, I checked my web browser [chrome://net-internals/#dns] and found that last year on November 20th, it accessed two IP addresses that are on the Grizzley-Steppe list: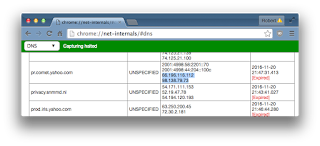 No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati |
Yahoo APT 29 APT 28 | |||
| 2017-01-02 16:29:22 | U.S. Gov\'s "GRIZZLY STEPPE" Report Fails to Achieve Purpose: Experts (lien direct) | The recently released Joint Analysis Report (JAR) published by the Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) to detail tools used by Russian hackers in cyber attacks against the United States election didn't deliver on its promise, security experts argue. | APT 29 APT 28 | |||
| 2016-12-30 19:30:10 | FBI-DHS Report Links Fancy Bear Gang to Election Hacks (lien direct) | Joint report “Grizzly Steppe†implicates Russian hacking group Fancy Bear in U.S. election-related hacking. | APT 29 APT 28 | |||
| 2016-12-29 20:40:33 | Some notes on IoCs (lien direct) | Obama "sanctioned" Russia today for those DNC/election hacks, kicking out 35 diplomats, closing diplomatic compounds, seizing assets of named individuals/groups. They also published "IoCs" of those attacks, fingerprints/signatures that point back to the attackers, like virus patterns, file hashes, and IP addresses.These IoCs are of low quality. They are published as a political tool, to prove they have evidence pointing to Russia. They have limited utility to defenders, or those publicly analyzing attacks.Consider the Yara rule included in US-CERT's "GRIZZLY STEPPE" announcement: What is this? What does this mean? What do I do with this information?It's a YARA rule. YARA is a tool ostensibly for malware researchers, to quickly classify files. It's not really an anti-virus product designed to prevent or detect an intrusion/infection, but to analyze an intrusion/infection afterward -- such as attributing the attack. Signatures like this will identify a well-known file found on infected/hacked systems.What this YARA rule detects is, as the name suggests, the "PAS TOOL WEB KIT", a web shell tool that's popular among Russia/Ukraine hackers. If you google "PAS TOOL PHP WEB KIT", the second result points to the tool in question. You can download a copy here [*], or you can view it on GitHub here [*].Once a hacker gets comfortable with a tool, they tend to keep using it. That implies the YARA rule is useful at tracking the activity of that hacker, to see which other attacks they've been involved in, since it will find the same web shell on all the victims.The problem is that this P.A.S. web shell is popular, used by hundreds if not thousands of hackers, mostly associated with Russia, but also throughout the rest of the world (judging by hacker forum posts). This makes using the YARA signature for attribution problematic: just because you found P.A.S. in two different places doesn't mean it's the same hacker.A web shell, by the way, is one of the most common things hackers use once they've broken into a server. It allows further hacking and exfiltration traffic to appear as normal web requests. It typically consists of a script file (PHP, ASP, PERL, etc.) that forwards commands to the local system. There are hundreds of popular web shells in use.We have little visibility into how the government used these IoCs. IP addresses and YARA rules like this are weak, insufficient for attribution by themselves. On the other hand, if they've got web server logs from multiple victims where commands from those IP addresses went to this specific web shell, then the attribution would be strong that all these attacks are by the same actor.In other words, these rules can be a reflection of the fact the government has excellent information for attribution. Or, it could be a reflection that they've got only weak bits and pieces. It's impossible for us outsiders to tell. IoCs/signatures are fetishized in the cybersecurity community: they love the small rule, but they ignore the complexity and context around the rules, often misunderstanding what's going on. (I've written thousands of the things -- I'm constantly annoyed by the ignorance among those not understanding what they mean).I see on What is this? What does this mean? What do I do with this information?It's a YARA rule. YARA is a tool ostensibly for malware researchers, to quickly classify files. It's not really an anti-virus product designed to prevent or detect an intrusion/infection, but to analyze an intrusion/infection afterward -- such as attributing the attack. Signatures like this will identify a well-known file found on infected/hacked systems.What this YARA rule detects is, as the name suggests, the "PAS TOOL WEB KIT", a web shell tool that's popular among Russia/Ukraine hackers. If you google "PAS TOOL PHP WEB KIT", the second result points to the tool in question. You can download a copy here [*], or you can view it on GitHub here [*].Once a hacker gets comfortable with a tool, they tend to keep using it. That implies the YARA rule is useful at tracking the activity of that hacker, to see which other attacks they've been involved in, since it will find the same web shell on all the victims.The problem is that this P.A.S. web shell is popular, used by hundreds if not thousands of hackers, mostly associated with Russia, but also throughout the rest of the world (judging by hacker forum posts). This makes using the YARA signature for attribution problematic: just because you found P.A.S. in two different places doesn't mean it's the same hacker.A web shell, by the way, is one of the most common things hackers use once they've broken into a server. It allows further hacking and exfiltration traffic to appear as normal web requests. It typically consists of a script file (PHP, ASP, PERL, etc.) that forwards commands to the local system. There are hundreds of popular web shells in use.We have little visibility into how the government used these IoCs. IP addresses and YARA rules like this are weak, insufficient for attribution by themselves. On the other hand, if they've got web server logs from multiple victims where commands from those IP addresses went to this specific web shell, then the attribution would be strong that all these attacks are by the same actor.In other words, these rules can be a reflection of the fact the government has excellent information for attribution. Or, it could be a reflection that they've got only weak bits and pieces. It's impossible for us outsiders to tell. IoCs/signatures are fetishized in the cybersecurity community: they love the small rule, but they ignore the complexity and context around the rules, often misunderstanding what's going on. (I've written thousands of the things -- I'm constantly annoyed by the ignorance among those not understanding what they mean).I see on |
APT 29 APT 28 | |||
| 2016-12-29 17:00:00 | FBI, DHS Report Implicates Cozy Bear, Fancy Bear In Election-Related Hacks (lien direct) | US government dubs the operation "GRIZZLY STEPPE" in new Joint Analysis Report, and says the malicious groups' activity continues. | APT 29 APT 28 | |||
| 2016-11-27 19:24:01 | Scapy vs. CozyDuke, (Sun, Nov 27th) (lien direct) | In continuation of observations from my GIAC Security Expert re-certification process, Ill focus here on a GCIA-centric topic: Scapy. Scapy is essential to the packet analyst skill set on so many levels. For your convenience, the Packetrix VM comes preconfigured with Scapy and Snort, so youre ready to go out of the gate if youd like to follow along for a quick introduction. Scapy is a powerful interactive packet manipulation program. It is able to forge or decode packets of a wide number of protocols, send them on the wire, capture them, match requests and replies, and much more. This includes the ability to handle most tasks such as scanning, tracerouting, probing, unit tests, attacks or network discovery, thus replacing functionality expected from hping, 85% of nmap, arpspoof, tcpdump, and others. If youd really like to dig in, grab TJ OConnors Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers (you should already have it), as first discussed here in January 2013. TJ loves him some Scapy: Detecting and Responding to Data Link Layer Attacks is another reference. :-) You can also familiarize yourself with Scapys syntax in short order with the SANS Scapy Cheat Sheet as well. Judy Novaks SANS GIAC Certified Intrusion Analyst Day 5 content offers a nice set of walk-throughs using Scapy, and given that it is copyrighted and private material, I wont share them here, but will follow a similar path so you have something to play along with at home. Well use a real-world APT scenario given recent and unprecedented Russian meddling in American politics. According to SC Magazine, Russian government hackers apparently broke into the Democratic National Committee (DNC) computer systems in infiltrations believed to be the work of two different Russian groups, namely Cozy Bear/ CozyDuke/APT 29 and Fancy Bear/Sofacy/APT 28, working separately. As is often the case, ironically and consistently, one the best overviews of CozyDuke behaviors comes via Kaspersky">syn = IP(src=10.0.2.15, dst=209.200.83.43)/TCP(sport=1337, dport=80, flags=S)/GET /ajax/index.php HTTP/1.1">wrpcap(/tmp/CozyDukeC2GET.pcap, syn), as seen in Figure 2. ">ls(IP). ">Figure 4: ls() If you">|">@holisticinfosec (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. | APT 29 APT 28 | |||
| 2016-11-11 01:10:14 | Warning: Beware of Post-Election Phishing Emails Targeting NGOs and Think Tanks (lien direct) | Just a few hours after Donald Trump won the 2016 US Presidential Election, a hacking group launched a wave of cyber attacks targeting U.S.-based policy think-tanks with a new spear phishing campaign designed to fool victims into installing malware.
The group of nation-state hackers, also known as Cozy Bear, APT29, and CozyDuke, is the one of those involved in the recent data breach of the
|
APT 29 | |||
| 2016-11-10 15:55:00 | Russian Hackers Behind DNC Breach Wage Post-US Election Attacks (lien direct) | Less than six hours after Donald Trump was named President-Elect of the US, Cozy Bear/APT29/CozyDuke nation-state hackers kicked off waves of spearphishing attacks. | APT 29 | |||
| 2016-11-10 11:46:16 | Suspected Russian hackers target US think tanks after election (lien direct) | Hours after Donald Trump won the presidential election, a suspected Russian cyberespionage team was blamed for targeting several U.S. think tanks with phishing emails designed to fool victims into installing malware.On Wednesday, the phishing emails landed in the inboxes of dozens of targets associated with U.S. think tanks and non-governmental organizations, said security firm Volexity.A hacking group called APT 29 or Cozy Bear was behind the attack, according to Veloxity. This is one of the same groups that security experts say was also responsible for hacking the Democratic National Committee and is allegedly tied to the Russian government.To read this article in full or to leave a comment, please click here | APT 29 | |||
| 2016-09-09 15:53:24 | The Dukes R&D Finds a New Anti-Analysis Technique (lien direct) | Threat actors constantly hunt for evasion and anti-analysis techniques in order to increase the success rate of their attacks and to lengthen the duration of their access on a compromised system. In some cases, threat… | APT 29 | |||
| 2016-08-30 10:30:00 | US Think Tanks Involved in Russia Research Allegedly Hacked (lien direct) | Russia-backed DNC hacker COZY BEAR behind these spearphish attacks on individuals and organizations, says CrowdStrike. | APT 29 | |||
| 2016-08-29 20:55:31 | Cozy Bear suspected of hacking Russia-focused think tanks in D.C. (lien direct) | The same cybergang that launched attacks against the Pentagon, State Department and DNC is also believed to have targeted Russia-focused think tanks in the U.S. |
APT 29 | |||
| 2016-06-21 13:04:21 | Guccifer 2.0 out - Cozy Bear, Fancy Bear hacked DNC, Fidelis analysis shows (lien direct) | A comparative analysis by Fidelis Cybersecurity of malware samples provided by the DNC supported findings by CrowdStrike that a pair of intrusions were the handiwork of the Cozy Bear and Fancy Bear APT groups purported to have ties to Russian intelligence. |
APT 29 APT 28 |
To see everything:
Our RSS (filtrered)
